A computer or network firewall is the first line of defense in safeguarding computer and networking resources. At a basic level a firewall works by filtering incoming and outgoing traffic based on predefined rules. From simple packet filtering to advanced deep packet inspection, firewalls help prevent unauthorized access and minimize the risk of cyberattacks.
In this blog post, I will explore what a computer firewall is, how it works, and its benefits and limitations.
What is a Firewall?
A firewall is a tool, either software or hardware that monitors and filters traffic that flows through it. Firewalls can be used to protect both applications and networks by regulating incoming and outgoing traffic based on a set of predefined rules.
The term “firewall” was borrowed from the construction industry, where a firewall is a physical barrier designed to contain the spread of fire within a building.
Essentially, a firewall acts as a virtual barrier between trusted and untrusted. Firewalls help protect against unauthorized access, data breaches, and various cyber threats by filtering out malicious traffic and allowing only legitimate data to pass through.
There are various types of firewalls, including hardware, software, and cloud-based solutions.
- Hardware firewalls are physical devices installed between a network and the internet.
- Software firewalls run on individual computers or servers within a network.
- Cloud firewalls, also known as Firewall-as-a-Service (FaaS), provide network security through a cloud service provider, offering scalable and easily manageable protection.
Evolution of Firewalls and Types
The first router including a firewall was introduced by Digital Equipment Corporation (DEC) in the 1980s. This router was designed to filter packets based on rules, such as not allowing traffic on a specific port.
Note: Below is an infographic on firewall evolution over the years.
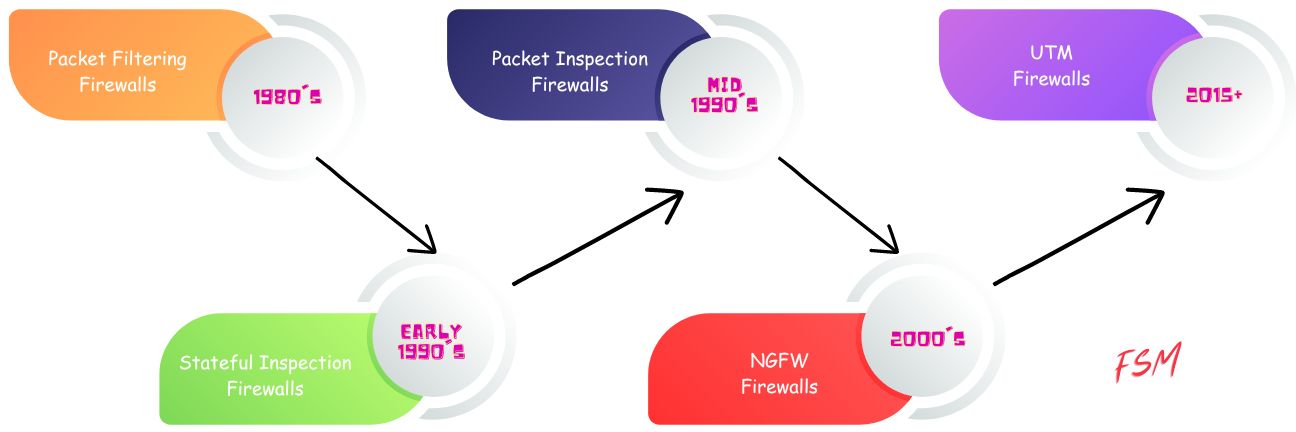
Let’s go over general technical features for each generation of firewalls.
- Packet filtering: The first generation of firewalls used packet filtering to limit access. These firewalls operated at the network layer and filtered connections based on the source and destination IP addresses, ports, and protocols. Packet filtering firewalls only provided basic protection, as they were relatively easy to bypass.
- Stateful inspection firewalls: The next generation of firewalls, added the ability to track the state of network connections. By monitoring the entire lifecycle of a connection, stateful inspection firewalls could better differentiate between legitimate and malicious traffic, offering improved security compared to their predecessors.
- Application layer firewalls: The third-gen firewalls improved upon the earlier technology by inspecting the content of the network traffic at the application layer. These firewalls are capable of understanding specific application protocols and could make decisions based on the actual data being transmitted. The level of inspection provides better protection against application-level attacks, such as SQL injection and cross-site scripting.
- Next-generation firewalls (NGFWs): NGFW firewalls incorporate comprehensive network security features. NGFWs combine traditional firewall functionality with intrusion detection and prevention systems (IDPS), deep packet inspection, application awareness, and other advanced capabilities. These firewalls can identify and block sophisticated threats, provide granular control over application usage, and integrate with other security tools to offer a multi-layered defense against cyberattacks.
The most recently Unified Threat Management (UTM) firewalls are being introduced. These all-in-one solutions combine traditional firewall functions with other security features such as antivirus, antispam, and content filtering. UTM firewalls are designed to provide comprehensive protection against a wide range of cyber threats. Vendors such as Allied Telesis and Sonic Wall are offering advanced UTM firewalls.
Check my post discussing Different Types of Firewalls and Top Vendors Selling Firewall Products.
How Does a Firewall Work?
In this section, Let’s look at the core principles behind how firewalls work and their various functions.
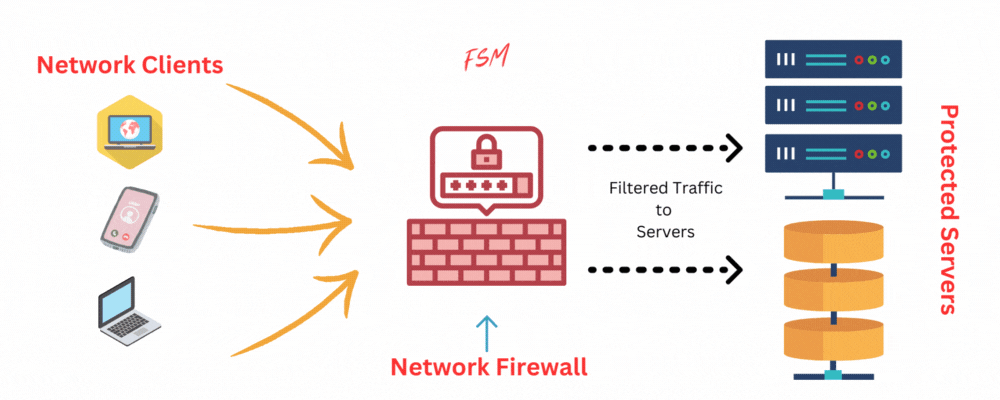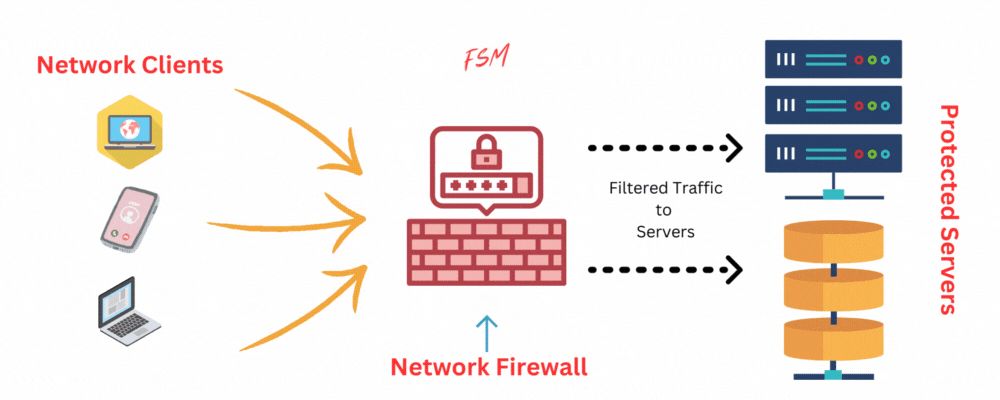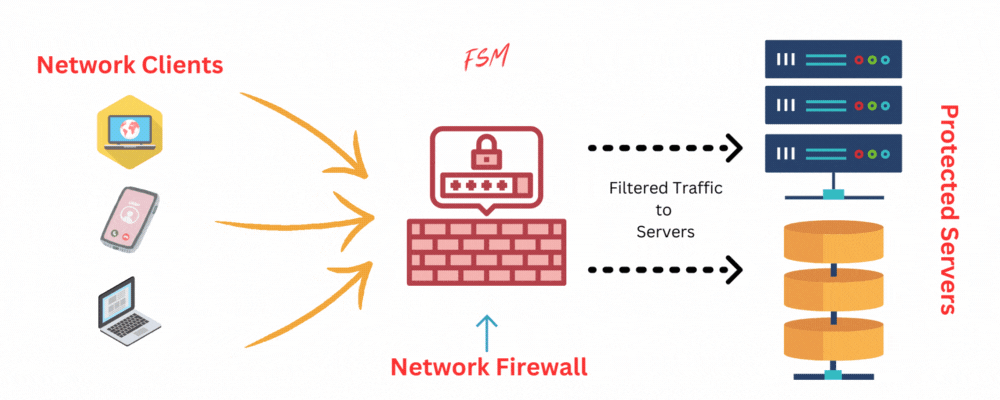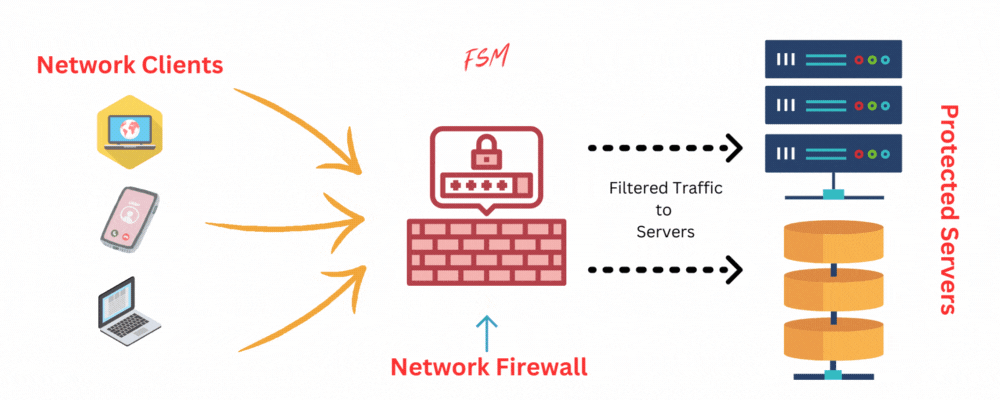
- Firewall Rules and Policies: Using rules and policies you can define the criteria which a firewall then uses to allow or deny network access. These rules are typically based on factors such as source and destination IP addresses, port numbers, protocols, and even application types. The firewall then uses these rules to make decisions about whether to permit or block network traffic.
- Packet Inspection and Analysis: Firewalls analyze incoming and outgoing packets to determine if they meet the established criteria for allowed traffic. Basic packet-filtering firewalls only examine packet headers, while more advanced firewalls like stateful inspection firewalls can also analyze packet payloads and track the state of network connections.
- Network Address Translation (NAT) and Firewalls: Many firewalls also incorporate Network Address Translation (NAT) functionality which allows a firewall to map multiple internal IP addresses to a single external IP address. By hiding the internal network from the outside world provides an additional layer of security by making it more difficult for attackers to target specific devices.
- Handling Blocked or Flagged Traffic: When a firewall detects traffic that violates its rules it either drops the offending network packets or just simply drops the connection. Advanced firewalls take more proactive measures, such as blocking the offending IP address that generates repeated malicious traffic. In extreme cases, a firewall can completely block the whole (sub)network that the traffic is coming from.
- Integration with External Security Tools: Firewalls can integrate with other security tools to provide a more comprehensive protection for computer networks. For example, next-generation firewalls (NGFWs) and unified threat management (UTM) firewalls can incorporate antivirus, antispam, and intrusion prevention systems (IPS) to detect and mitigate a wide range of threats.
How are Firewalls Used?
Nowadays firewalls are commonly used across most corporate networks. Almost all personal computers are also using software based firewall solutions as well.
Listed below are key use cases of firewalls.
- Secure Internal Networks: Firewalls are commonly deployed at the edge of an organization’s internal network, separating it from external networks. By filtering inbound and outbound traffic based on predefined rules, firewalls prevent unauthorized users and malicious traffic from entering the internal network, thereby protecting sensitive data and resources.
- Protect Individual Devices: Software-based firewalls can be installed on individual devices, such as desktop computers, laptops, and servers, to provide an additional layer of security. These firewalls monitor and control network traffic to and from the device, helping to prevent unauthorized access, data exfiltration, and malware infections.
- Virtual Private Networks (VPNs): Firewalls can also be used in conjunction with VPNs to secure remote connections between an organization’s internal network and offsite employees or branch offices. By encrypting the data transmitted over the internet and using the firewall to enforce access control policies, VPNs provide a secure communication channel for remote users.
- Segregating Network Zones: Firewalls can be used to create separate network zones within an organization, each with its own security policies and access controls. For example, a company might use firewalls to segment its internal network into zones for human resources, finance, and research and development, thereby restricting access to sensitive data and resources based on user roles and permissions.
- Intrusion Prevention and Detection (IDS): Some advanced firewalls, such as next-generation firewalls (NGFWs) and unified threat management (UTM) firewalls, incorporate intrusion prevention and detection capabilities. These firewalls can detect and block known attack patterns, malware signatures, and other threats in real-time, providing proactive protection against cyberattacks.
- Application Control and Visibility: Next-generation firewalls (NGFWs) provide granular control over network traffic at the application level. By identifying and controlling access to specific applications, firewalls can help organizations enforce security policies, prevent unauthorized software usage, and optimize network performance.
- Compliance and Regulatory Requirements: Firewalls play an essential role in helping organizations meet compliance and regulatory requirements related to data protection and cybersecurity. By implementing robust access controls, traffic filtering, and logging capabilities, firewalls can help demonstrate compliance with industry-specific regulations, such as HIPAA, PCI DSS, and GDPR.
Firewall Deployment Options
Firewall deployment options vary depending on an organization’s network infrastructure and security requirements. Here are the main firewall deployment options to consider:
Edge Firewall
An edge firewall is placed at the perimeter of a network, separating the internal network from and external networks. T
his type of deployment provides a first line of defense against external threats, filtering inbound and outbound traffic based on predefined rules and policies.
Internal Segmentation Firewall (ISFW)
ISFWs are deployed within an organization’s internal network to create separate security zones or segments.
By isolating different parts of the network, ISFWs can help prevent the lateral movement of threats and unauthorized access to sensitive data and resources.
Host-based Firewall
A host-based firewall is a software that runs on individual devices, such as desktop computers, laptops, or servers.
This type of firewall monitors and controls network traffic to and from the host system, adding an additional layer of security.
Virtual Firewall
Virtual firewalls are similar to host-based solutions but they run within virtualized environments, such as private or public cloud infrastructure.
These firewalls provide network security for virtual machines (VMs) and can be easily scaled and managed to accommodate changing network demands.
Managed Firewall Service
A managed firewall service is a solution where an external provider is responsible for the deployment, management, and monitoring of a firewall on behalf of an organization.
This option is well-suited for businesses that lack the necessary resources or expertise to manage their own firewalls and can help reduce the burden of ongoing maintenance and support.
Unified Threat Management (UTM) Firewall
UTM firewalls are all-in-one security appliances that combine traditional firewall functions with additional security features.
This deployment option is often used by small and medium-sized businesses (SMBs) that require a single, easy-to-manage security solution.
Best Practices For Managing And Maintaining Firewalls
Effective firewall management involves monitoring, updating, and optimizing firewall rules and configurations, as well as integrating the firewall with other security tools and processes. Listed below are some best practices for managing a firewall based network.
- Apply Firmware and Software Updates: Firewalls, like any other hardware or software, require regular updates to fix security vulnerabilities, improve performance, and add new features.
- Backup and Disaster Recovery: Regularly back up firewall configurations and rules to facilitate a quick recovery in case of hardware failure, configuration errors, or other issues. Maintain a disaster recovery plan in place to ensures that procedures to restore access are clearly documented.
- Employee Training and Awareness: Ensuring that employees understand the importance of network security and the role of firewalls is crucial for maintaining a secure environment. Regular training and awareness programs can help employees recognize potential threats, such as phishing attacks or social engineering.
- Monitor Firewall Performance and Logs: Monitoring firewall performance and logs helps to identify potential issues, such as bottlenecks, misconfigurations, or security incidents. By analyzing logs and performance data, one can detect and respond to potential threats more quickly.
- Regularly Update Firewall Rules and Policies: Ensure that you regularly update firewall rules and policies. This ensures that the firewall remains effective in blocking unauthorized access and mitigating potential threats.
- Periodic Security Audits: Conducting periodic security audits helps identify potential vulnerabilities and gaps in an organization’s security posture. These audits should include a thorough review of firewall rules, configurations, and performance data, as well as assessments of the organization’s overall network security strategy.
Future of Firewalls and Network Security
Let’s look at the technologies and features making inroads with respect to firewalls and network security.
Advanced Threat Intelligence and Analytics
Firewalls will increasingly rely on advanced threat intelligence and analytics to detect and respond to sophisticated cyber threats. By leveraging large-scale data analysis, machine learning, and real-time threat intelligence feeds, firewalls will be able to make more informed decisions about network traffic, helping organizations stay one step ahead of potential attacks.
Artificial Intelligence and Machine Learning
AI and ML are poised to revolutionize network security by automating threat detection, analysis, and response. Firewalls equipped with AI and ML capabilities will be able to identify and block new and emerging threats in real-time, adapting to ever-changing attack vectors and techniques. This will enable organizations to proactively defend against cyberattacks, reducing the risk of breaches and minimizing the time required to respond to incidents.
Cloud Native Firewalls
As organizations continue to migrate their workloads to the cloud, cloud-native firewalls will become increasingly important in securing cloud-based infrastructure and applications. These firewalls will be designed specifically for cloud environments, providing scalable, flexible, and easily manageable security solutions that can be seamlessly integrated with other cloud-based services.
Enhanced Privacy and Data Protection
In response to growing concerns about data privacy and protection, firewalls will need to incorporate advanced data protection features, such as encryption, data loss prevention (DLP), and privacy-by-design principles. This will help organizations comply with data protection regulations and maintain the trust of their customers and stakeholders.
Increased Focus on IoT Security
With the rapid proliferation of IoT devices, securing these devices and the data they generate has become a critical concern. Firewalls will need to evolve to accommodate the unique requirements of IoT networks, such as handling increased network traffic, securing a wider variety of device types, and addressing new vulnerabilities associated with IoT devices.
Unified Security Management
As the security landscape grows more complex, organizations will increasingly seek unified security solutions that consolidate multiple security functions into a single platform. Next-generation firewalls and unified threat management (UTM) appliances will continue to evolve, incorporating additional security features and providing a centralized point of control for managing network security.
Zero Trust Security
The zero trust security model assumes that no user or device should be trusted by default, requiring continuous validation of trustworthiness before granting access to network resources. Firewalls will play a crucial role in implementing zero-trust security by enforcing granular access control policies, segmenting networks, and providing real-time visibility into network traffic.
Conclusion
Firewalls are a critical component of any organization’s cybersecurity strategy, providing a first line of defense against cyber threats and unauthorized access. In terms of network security, they provide the most bang for the buck invested. But it is important to recognize that firewalls are only one component of a comprehensive cybersecurity strategy.
Frequently Asked Questions
Why is a Firewall Important?
A firewall is important because it serves as the first line of defense in protecting computer networks and systems from unauthorized access and malicious attacks.
By monitoring and controlling incoming and outgoing network traffic based on predefined security rules, firewalls help prevent cybercriminals from exploiting vulnerabilities, stealing sensitive data, or launching denial-of-service attacks.
Additionally, firewalls can provide essential network security features such as Network Address Translation (NAT) and Virtual Private Network (VPN) support, which help maintain privacy and safeguard data transmission. In an era of increasing cybersecurity threats and evolving attack techniques, having a robust firewall in place is a critical component of a comprehensive and multi-layered security strategy.
How much does a firewall cost?
The cost of a firewall can vary significantly depending on factors such as the type of firewall, the size and complexity of the network it protects, and the specific features and capabilities it offers.
Hardware firewalls, for instance, can range from a few hundred dollars for basic home or small business models to several thousand dollars for enterprise-level appliances with advanced features. Software firewalls, on the other hand, can either be free, open-source solutions or require a subscription fee for commercial products.
Cloud-based firewalls often operate on a pay-as-you-go model, with costs determined by factors such as the amount of traffic and the number of protected resources.
Note: A consumer firewall such as one provided by Microsoft on the Windows operating system is available for free and includes the most important feature, which is the ability to block traffic by port or application.
What are the benefits of using firewalls?
Firewalls offer several benefits for securing networks and applications, including:
- Protection against unauthorized access and attacks: Firewalls prevent unauthorized access to a network or application by blocking traffic that does not meet the defined rules. This can help prevent attacks such as denial-of-service attacks, port scanning, and hacking attempts.
- Control over network traffic: Firewalls provide control over the traffic that enters and exits a network or application, allowing administrators to set rules for what is allowed and what is blocked. This can help optimize network performance and improve overall security.
- Increased network security and confidentiality: Firewalls provide an additional layer of security for networks and applications, helping to protect sensitive information and prevent data breaches. This can help businesses comply with regulations and prevent reputational damage.
What are the limitations of using firewalls?
While firewalls are a valuable tool for network security, they do have limitations. Some of the limitations of firewalls include:
- Cannot protect against all types of attacks: Firewalls are effective at protecting against network-based attacks, such as malware infections or unauthorized access attempts. However, firewalls cannot protect against all types of attacks, such as social engineering or physical breaches. This means adding additional security measures, may be needed to complement the firewall.
- May slow down network performance: Firewalls can slow down network performance, especially if they are configured with too many rules or if when the rules are complex. This can impact user productivity and overall network performance.
- Requires regular maintenance and updates: Firewalls require regular maintenance and updates to remain effective. This includes updating the firewall software, reviewing and updating firewall rules, and monitoring for new threats and vulnerabilities. Failure to perform these maintenance tasks can render the firewall ineffective and increase the risk of security breaches.