Firewalls are essential for protecting against cyber threats, acting as a barrier between trusted internal networks and untrusted external networks. They monitor and control network traffic based on predetermined security rules. Choosing the right type of firewall depends on factors like organization size, budget, and security needs.
There are various types of firewalls, each with unique features and strengths. In this post, I will explore these different types to help you make an informed decision about which firewall is best for your organization’s security requirements.
- Types of Firewalls
- Packet Filtering Firewalls
- Stateful Inspection Firewall
- Application Level or Proxy Firewalls
- Circuit Level Gateway Firewall
- Next Generation Firewalls (NGFW)
- Unified Threat Management Firewalls (UTM)
- Hardware vs. Software Firewalls
- Hardware vs. Software Firewalls – A Comparison
- Companies Providing Hardwall and Software Firewall Solutions
- Conclusion
- References
Types of Firewalls
Firewalls play a crucial role in maintaining the security of computer networks. Over time, different types of firewalls have been developed to address various security needs and challenges. Here, we will discuss the main types of firewalls and their unique features.
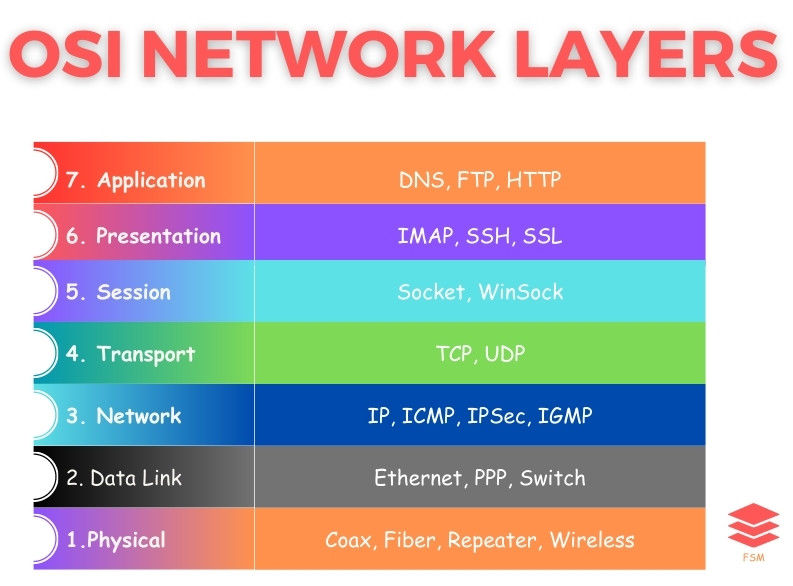
Packet Filtering Firewalls
Packet-filtering firewalls are the simplest type of firewall, operating at the network layer 3, of the OSI (Open Systems Interconnection) model. Their primary function is to inspect individual data packets and determine whether they should be allowed or denied based on predefined rules.
These rules are typically established by network administrators and are based on parameters such as the source and destination IP addresses, port numbers, and protocols.
The advantages of packet filtering firewalls include their simplicity, low cost, and high performance. Since they only examine the packet header information, they are fast and efficient.
However, packet-filtering firewalls have several limitations.
- Unable to track the state of network connections, making them more susceptible to attacks that exploit vulnerabilities in the firewall rules
- Packet-filtering firewalls lack the ability to inspect the content of data packets, which means they cannot identify application-specific attacks or block traffic based on application-specific rules
Packet-filtering firewalls are fast and efficient but they may not be suitable for more complex network environments where higher levels of security measures are required.
Stateful Inspection Firewall
Stateful inspection firewalls, offer a more sophisticated protection than the packet-filtering firewalls. These firewalls operate at both the network and transport layers of the OSI model, allowing them to examine individual packets as well as maintain information about the state of active network connections.
The primary advantage of stateful inspection firewalls is their ability to keep track of the state of each network connection in a state table. When a packet arrives, the firewall checks the state table to determine if the packet belongs to an existing, established connection, otherwise, the network packet is dropped.
This approach provides several benefits:
- Improves the firewall’s performance by allowing established connections to bypass resource intensive rule-checking processes.
- Enhances security by blocking unsolicited incoming traffic that does not correspond to an existing connection, making it harder for attackers to exploit vulnerabilities or launch denial-of-service attacks.
Despite these advantages, stateful inspection firewalls have some limitations as they can struggle to handle protocols that may use dynamic port assignments. Furthermore, these firewalls are susceptible to resource exhaustion attacks.
Application Level or Proxy Firewalls
Application-level firewalls, aka proxy firewalls, provide a higher level of security compared to other types of firewalls by operating at the application layer of the OSI model.
These firewalls act as intermediaries between internal and external networks, effectively separating the protected network from the outside world. By intercepting and inspecting data packets at the application layer, proxy firewalls can prevent attacks that may otherwise bypass lower-level security measures.
Advantages of proxy firewalls:
- Access controls: Enforce granular access controls based on user identities, IP addresses, and specific application protocols. This provides fine-grained security policies that govern the flow of information between networks.
- Deep packet inspection: Analyze the contents of data packets and ensure they adhere to defined protocols. Deep inspection of traffic allows proxy firewalls to identify and block malicious content, such as malware, viruses, or unauthorized data transmissions.
- Network isolation: Ability to provide a level of anonymity for the protected network. Since external traffic is routed through the proxy, the true IP addresses of internal devices remain hidden, making it more difficult for attackers to target specific systems.
However, these security benefits come at a cost. Due to the additional processing required to inspect traffic at the application layer, proxy firewalls can introduce latency and reduce network performance. This may be a concern for organizations with high-bandwidth requirements or latency-sensitive applications.
Circuit Level Gateway Firewall
Circuit-level gateway firewalls, aka circuit-level proxies, are an intermediary type of firewall that operate at the session layer (5) of the OSI model. They establish a connection between the internal network and external networks, monitoring and regulating the establishment of TCP and UDP sessions.
Circuit-level gateways focus on ensuring that the communication between the two networks follows a set of predefined rules and protocols, rather than inspecting the content of the packets themselves.
Advantages of circuit-level gateway firewall:
- Provide a higher level of security compared to packet-filtering firewalls, without the performance overhead associated with application-level (proxy) firewalls.
- Capable of hiding the internal network’s IP addresses and other details from external networks.
- Quickly identify and block suspicious or malicious connections based on unusual traffic patterns or protocol violations.
One limitation of a circuit-level gateway firewall is that it cannot analyze the content of data packets and enforce application-specific policies as it does not inspect the contents of data packets flowing through it.
Next Generation Firewalls (NGFW)
NGFW firewalls represent a significant evolution in firewall technology, providing a more sophisticated and comprehensive approach to network security. Unlike traditional firewalls, NGFWs combine advanced features such as deep packet inspection, intrusion prevention systems (IPS), application awareness, and user identity tracking.
Features of Next Generation Firewalls.
- Application-aware: Identify and control access to specific applications, rather than merely blocking or allowing traffic based on IP addresses or ports.
- Deep packet inspection: NGFWs examine the entire contents of data packets, not just the header data. This in-depth analysis enables the firewall to detect and block malicious payloads or data exfiltration attempts that may otherwise bypass traditional firewalls.
- IPS: Incorporate intrusion prevention systems, which proactively identify and block known attack patterns, vulnerabilities, and exploits.
- Role-based access control (RBAC): This feature allows NGFWs to incorporate user information into their security policies, enabling more precise control over network access.
NGFWs offer a significant leap forward in network security technology, offering a more comprehensive and intelligent approach to protecting network access and assets.
Unified Threat Management Firewalls (UTM)
UTM firewalls offer an attractive solution for small and medium-sized businesses (SMBs) looking for a comprehensive and easy-to-manage security platform. These all-in-one systems combine the capabilities of traditional firewalls with a range of additional security features, including antivirus, antispam, content filtering, and intrusion prevention.
By integrating multiple security functions into a single appliance or software solution, UTM firewalls simplify network security management and reduce the complexity of deploying and maintaining multiple standalone security tools.
Advantages of UTM firewalls:
- provide a holistic approach to network security, addressing various threat vectors simultaneously.
- UTM firewalls reduce the need for IT staff to manage multiple security products.
Disadvantages of UTM firewalls:
- The all-in-one nature of these systems can sometimes lead to performance bottlenecks, particularly when dealing with high volumes of network traffic.
- Integration of multiple security features into a single solution may not always provide the same level of protection as specialized standalone tools.
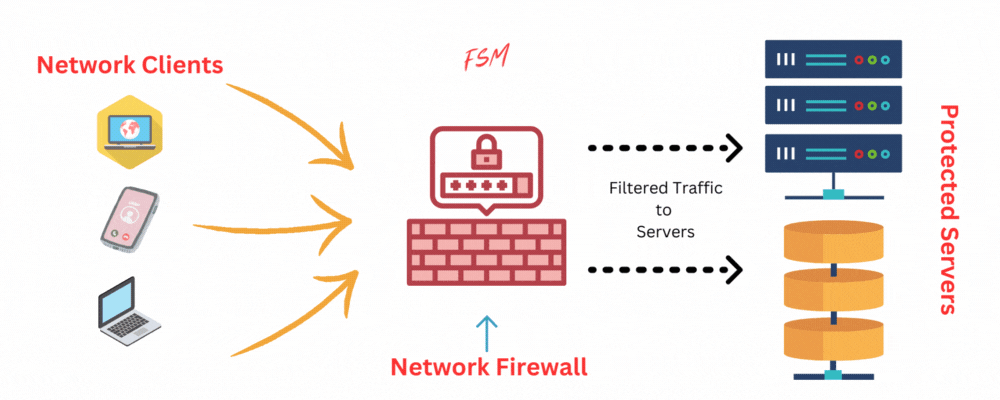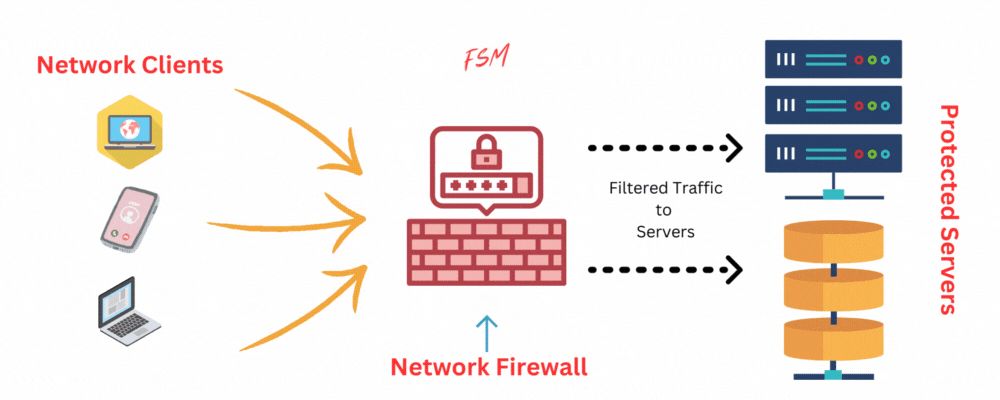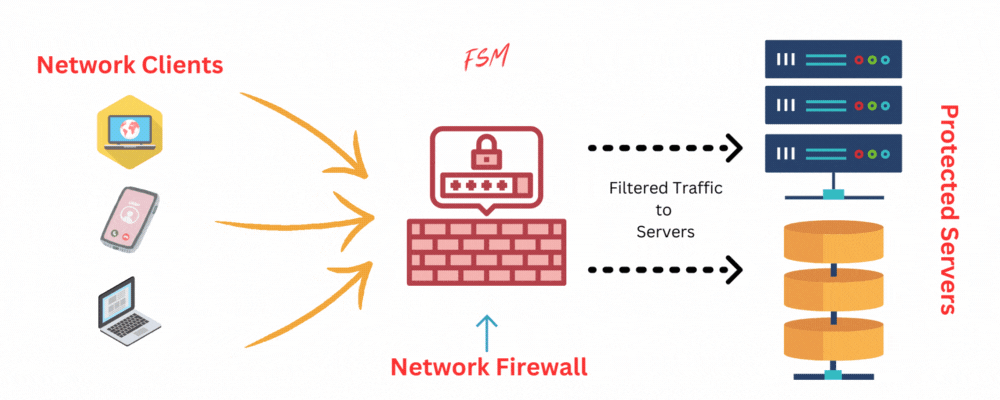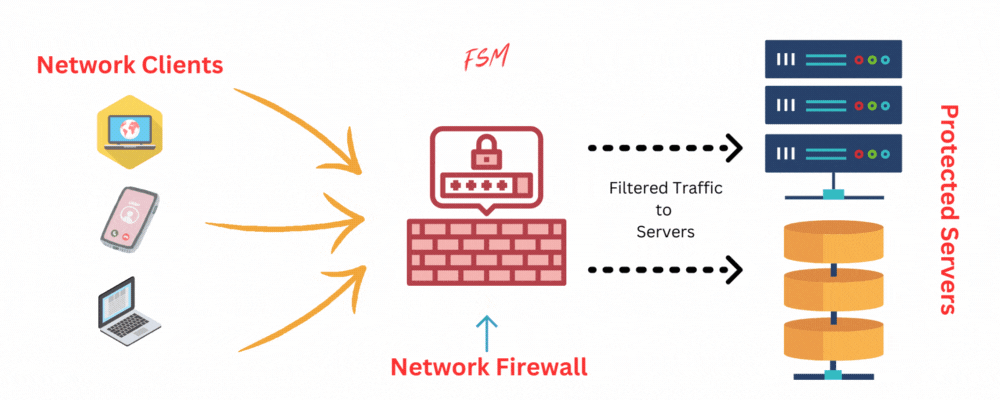
Hardware vs. Software Firewalls
Firewalls come in two primary forms: hardware firewalls and software firewalls. Each type has its own set of advantages and disadvantages, making them suitable for different situations and environments.
In this section, I will explore the differences between hardware and software firewalls, as well as their respective use cases.
Hardware Firewalls
Hardware firewalls are dedicated physical devices that are connected between an organization’s internal network and external networks, such as the Internet.
They are designed specifically for the purpose of filtering and controlling network traffic, providing a high level of security and performance.
| Advantages | Disadvantages |
|---|---|
| Performance Hardware firewalls are optimized for network traffic processing, which often results in better performance compared to software firewalls running on general-purpose hardware. | Cost Hardware firewalls are typically more expensive than software firewalls, and they require additional hardware resources to operate. They also provide limited customization options compared to software firewalls. |
| Scalability Many hardware firewalls can be easily scaled to accommodate growing network demands by adding additional modules or devices. | Physical Space and Maintenance Hardware firewalls require physical space for installation and ongoing maintenance, such as firmware updates and hardware replacement. |
| Centralized Management Hardware firewalls provide a centralized point of control for network security, simplifying management and monitoring tasks. | |
| Dedicated Resources Since hardware firewalls have their own dedicated resources, they do not consume processing power, memory, or storage on the host system. |
Software Firewalls
Software firewalls are applications that run on general-purpose computers or servers, monitoring and controlling network traffic on the host system. They can be installed on individual devices, such as desktop computers, laptops, or servers, providing an additional layer of security.
| Advantages | Disadvantage |
|---|---|
| Cost Software firewalls are generally less expensive than hardware firewalls, making them more accessible for small businesses and home users. | Complexity Managing multiple software firewalls on individual devices can be more complex and time-consuming than managing a centralized hardware firewall. |
| Flexibility Software firewalls can be easily updated, configured, and customized to meet the specific needs of the host system. | Performance Running a software firewall on a general-purpose system can consume processing power, memory, and storage, potentially affecting the performance of the host system. |
| Device-Level Protection By installing software firewalls on individual devices, organizations can provide an extra layer of security to protect against internal threats and unauthorized access. | |
| Ease of Deployment Software firewalls can be quickly deployed and do not require any additional physical space or hardware. |
Hardware vs. Software Firewalls – A Comparison
| Hardware Firewall | Software Firewall |
|---|---|
| Operates independently from the host computer | A physical device installed at the network perimeter |
| Centralized network security | Individual computer security |
| Operates independently from host computer | Relies on the resources of the host computer |
| Can handle a large number of simultaneous connections | Can slow down computer performance |
| Easier to configure and maintain | Require regular maintenance and updates |
| Provides limited customization options | Highly customizable |
| More expensive than software firewalls | Less expensive than hardware firewalls |
| Offers hardware-based encryption and decryption | No hardware-based encryption or decryption |
Companies Providing Hardwall and Software Firewall Solutions
In this sections let’s look at some of the companies providing cutting edge firewalls solutions for all types of enterprises.
You will find that for enterprise solutions most of the companies provoding hardwall firewall solutions are also engaged in software beased solutions as well.
On the other hand, companies selling consumer software firewall solutions usually stay away from hardware solutions as their products manily run on desktops and laptops.
Companies Selling Hardware Firewall Solutions
Here are ten examples of vendors providing hardware firewalls.
| Company | Description |
|---|---|
| Barracuda Networks | Barracuda Networks is a provider of cloud-enabled security and data protection solutions, offering hardware firewalls like their Barracuda CloudGen Firewall series. |
| Check Point Software | Check Point is a leading provider of cybersecurity solutions, offering a range of hardware firewall products, including their Check Point Quantum Security Gateway series. |
| Cisco Systems | Cisco is a well-known provider of networking equipment and security solutions, offering a range of hardware firewalls, including their Cisco Adaptive Security Appliance (ASA) series and Cisco Firepower Next-Generation Firewall (NGFW) series. |
| Fortinet | Fortinet specializes in network security and offers a variety of hardware firewall solutions, such as their FortiGate series of unified threat management (UTM) and next-generation firewalls (NGFWs). |
| Juniper Networks | Juniper Networks is well-known for its networking equipment and security solutions, providing a variety of hardware firewalls such as their Juniper Networks SRX Series Services Gateways. |
| NETGEAR | The NETGEAR ProSafe Firewall provides reliable, cost-effective network security with advanced features for small and medium-sized businesses, ensuring robust protection against cyber threats. |
| Palo Alto Networks | Palo Alto Networks is a leading provider of advanced cybersecurity solutions, including their popular line of next-generation firewalls (NGFWs) called the Palo Alto Networks PA Series. |
| SonicWall | SonicWall specializes in network security and offers a range of hardware firewall products, including their SonicWall TZ, NSA, and NSsp series. |
| Sophos | Sophos is a global cybersecurity company offering a variety of security solutions, including their Sophos XG Firewall and Sophos SG UTM hardware firewall products. |
| WatchGuard Technologies | WatchGuard Technologies focuses on network security and offers a range of hardware firewalls, such as their WatchGuard Firebox series. |
| Zyxel Communications | Zyxel Communications is a networking equipment and security solutions provider, offering a variety of hardware firewalls, including their Zyxel ZyWALL series. |
Companies Selling Software Firewall Solutions
Here are several vendors that provide enterprise software firewall solutions. Here are some of the most popular ones.
| Company | Description |
|---|---|
| Broadcom | Broadcom provide many software solutions for preventing cybersecurity threats. With their purchase of Symantec they have acquired a rnage of security solutions, including antivirus software and firewalls. Their software firewall solution provides advanced protection against cyber threats, including intrusion detection and prevention and application control. |
| Check Point Software | Check Point is a cybersecurity company that provides a range of network security solutions, including software firewalls. Their firewall solutions include Check Point Next Generation Firewall and Check Point CloudGuard. |
| Cisco Systems | Cisco is a leading provider of networking and cybersecurity solutions, including software firewalls. Their firewall solutions include Cisco Firepower Next-Generation Firewall and Cisco Adaptive. |
| Comodo | Comodo is a cybersecurity company that provides a range of security solutions, including a free and open-source software firewall. Comodo Firewall provides comprehensive protection against cyber threats, including intrusion detection and prevention, application control, and sandboxing. |
| Fortinet | Fortinet is a cybersecurity company that provides a range of network security solutions, including software firewalls. Their firewall solutions include FortiGate Next-Generation Firewall and FortiWeb Web Application Firewall. |
| Juniper Networks | Juniper Networks is a networking and cybersecurity company that provides a range of network security solutions, including software firewalls. Their firewall solutions include Juniper Networks SRX Series Services Gateways and Juniper Networks vSRX Virtual Firewall. |
| Kaspersky | Kaspersky is a global cybersecurity company that provides a range of security solutions for individuals and organizations. Their software firewall solution provides advanced protection against cyber threats, including malware and viruses. |
| McAfee | McAfee is a global cybersecurity company that provides a range of security solutions for individuals and organizations. Their software firewall solution provides advanced protection against cyber threats, including malware and viruses. |
| Norton | Norton is a well-known cybersecurity company that provides a range of security solutions, including antivirus software and firewalls. Norton Firewall is included in their Norton Internet Security suite and provides advanced protection against various types of cyber threats. |
| Sophos | Sophos is a cybersecurity company that provides a range of security solutions for organizations of all sizes. Their software firewall solution provides advanced protection against cyber threats, including malware and viruses, and includes features such as application control and web filtering. |
| WatchGuard Technologies | WatchGuard Technologies is a cybersecurity company that provides a range of network security solutions, including software firewalls. Their firewall solutions include WatchGuard Firebox Firewall and WatchGuard Cloud Firewall. |
| ZoneAlarm | ZoneAlarm is a software firewall solution provided by Check Point Software Technologies. It provides advanced protection against cyber threats, including anti-phishing and anti-spam protection, intrusion detection and prevention, and application control. |
Conclusion
A firewall provides the cheapest form of protection against a network security attack. Make sure you always have one in place and keep it up to date with security patches and effective rules.
Choosing the right type of firewall is essential for network protection against cyber threats.