In this post, I will go over the details of setting up Linux UFW firewall on Linux systems such as Ubuntu, Red Hat, Fedora and CentOS.
The growth of the internet has given rise to malicious players attacking its infrastructure. Security threats such as hacking and malware attacks have become more prevalent and sophisticated over the years.
Due to this increase in attacks, the need for protecting systems and networks has gone up. This is given rise to the use of firewalls to reduce the attack surface of systems.
A firewall also protects against hacking attempts that you port scanning techniques.
See Also
A firewall can be hardware or software-based. UFW software is available for free to use on Linux systems and uses IP Tables in the backend. It helps to prevent unauthorized inbound and outbound access.
- What is a Firewall?
- What is UFW?
- Installing UFW on Linux
- Basic UFW Commands
- Manage UFW Service Access By Service Name
- Manage UFW Access By Port Number and Type
- How to Setup UFW Access Rules for IP Address
- Advanced UFW Firewall Configuration
- Limiting Connections on Specific Ports
- Customize UFW Settings
- Adding UFW Application Profiles
- Conclusion
What is a Firewall?
A firewall is either a software or hardware component that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between a trusted internal network and untrusted external networks. Firewall uses Port and IP address traffic filtering based on configured rules.
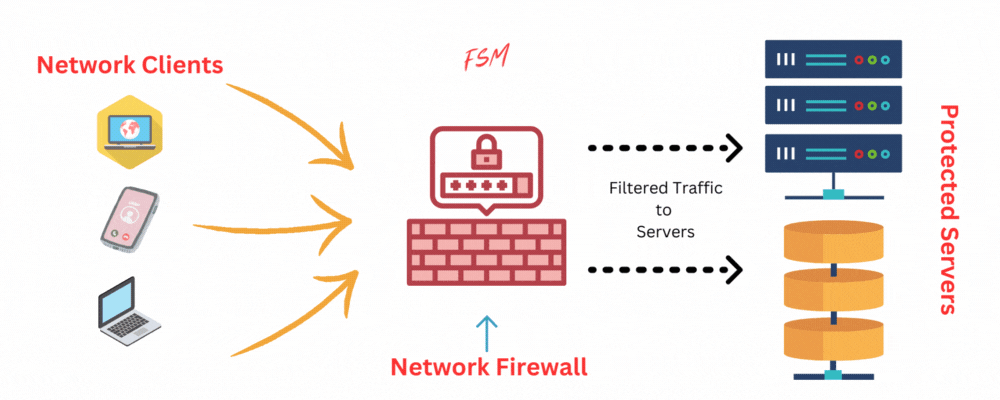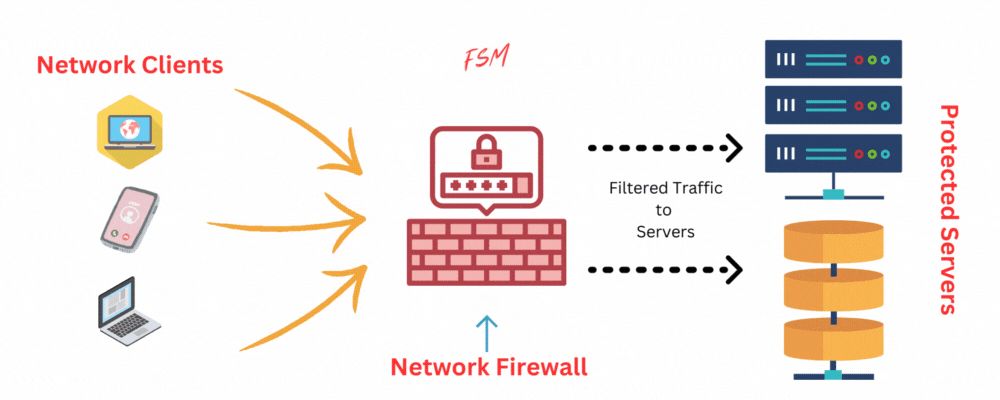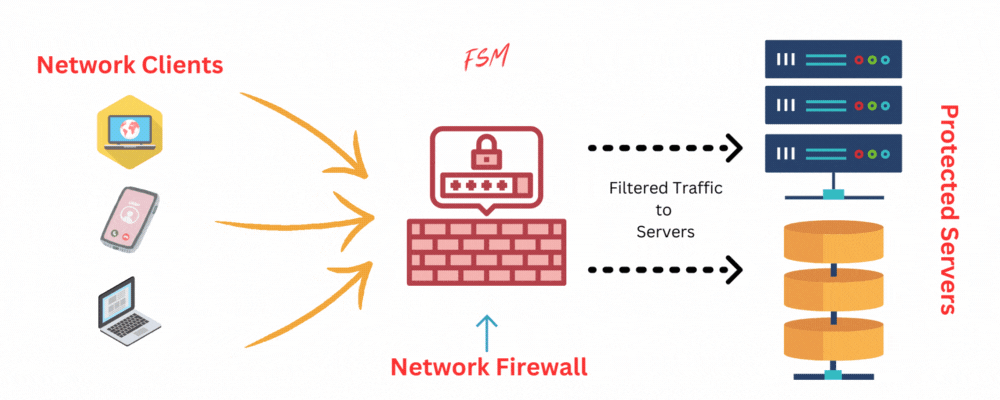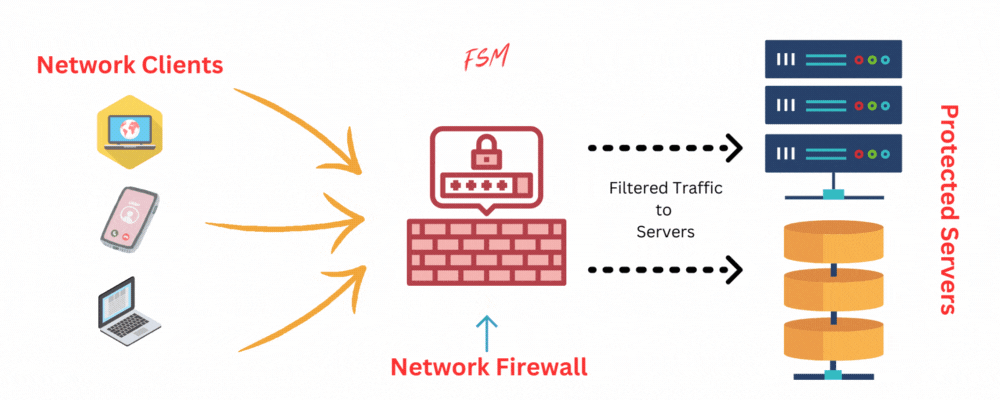
What is UFW?
UFW is a software firewall configuration tool for Linux systems. It is a command line tool that is used to setup IP and Port filtering rules on Linux distributions such as Ubuntu, Debian, CentOS, and Fedora.
Installing UFW on Linux
Before using ufw command to configure firewall rules we need to make sure that it is installed and configured. To check if ufw is installed, enter the command below in the terminal widow:
root@slap:/home/user# sudo ufw status
Status: inactiveIf UFW package is installed, you will see a message that will show the status. In my case, the firewall is not active, but it is installed.
In case you run into an error saying something like “command not found”, then you have to install UFW package.
You can install UFW package on Ubuntu using the command:
sudo apt-get install ufwSetting Up UFW is pretty straightforward and should not take very long.
You can do makes changes to firewall configuration irrespective of the run status of ufw.
Let’s start using it.
Basic UFW Commands
Let’s start with a couple of ufw admin options.
How to Enable UFW
Enabling UFW To enable UFW, enter the following command in the terminal window:
root@d1:/home/user# sudo ufw enable
Firewall is active and enabled on system startupThis command turns on the firewall and enables it to start automatically at boot time.
How to Disable UFW
Disabling UFW To disable UFW, type the following command in the terminal window:
root@d1:/home/user# sudo ufw disable
Firewall stopped and disabled on system startupThis command turns off the firewall and disables it from starting automatically at boot time.
How to Check UFW Status
Checking UFW Status To check the status of UFW, type the following command in the terminal window:
sudo ufw statusThis command shows the current status of UFW, including the active and inactive status of the firewall.
Manage UFW Service Access By Service Name
Allowing Incoming Traffic By default, UFW blocks all incoming traffic. However, there may be times when you need to allow incoming traffic to a specific port. To allow incoming traffic, you can use the UFW command followed by the port number and the protocol.
How to Enable UFW Access For a Service
Allowing SSH Access To allow SSH access, which uses port 22, enter the following command in the terminal window:
root@d1:/home/user# sudo ufw allow ssh
Rules updated
Rules updated (v6)This command allows incoming SSH traffic to your Linux system. Rules for both IPv4 and IPv6 are updated to allow access.
Allowing HTTP Access To allow HTTP access, which uses port 80 by default, enter the following command in the terminal window:
root@d1:/home/user# sudo ufw allow http
Rules updated
Rules updated (v6)This command allows incoming HTTP traffic to your Linux system.
How to Deny UFW Access For a Service
Sometimes, you may want to deny incoming traffic to a specific port. To deny incoming traffic, you can use the UFW command followed by the port number and the protocol.
Deny SSH Access
To deny SSH access, which uses port 22, enter the following command in the terminal window:
root@d1:/home/user# sudo ufw deny ssh
Rules updated
Rules updated (v6)This updates the rules to disallow access to ssh port. I think it would make more sense if the reply also stated that access is denied.
Deny Access to HTTP
To deny HTTP access, which uses port 80, enter the following command in the terminal window:
root@d1:/home/user# sudo ufw deny http
Rules updated
Rules updated (v6)Manage UFW Access By Port Number and Type
You can also set up rules to allow or deny traffic to specific ports.
How to Enable UFW Access By Port Number
To allow traffic to a specific port, the following command format is used.
sudo ufw allow [port]/[protocol]Replace [port] with the port number and [protocol] with the protocol used by the service.
For example, to allow traffic to port 8080, type the following command:
root@d1:/home/user# sudo ufw allow 8080/tcp
Rules updated
Rules updated (v6)How to Disable UFW Access By Port Number
To deny traffic to a specific port, use the following optiosn with the ufw command.
sudo ufw deny [port]/[protocol]Replace [port] with the port number and [protocol] with the protocol used by the service.
For example, to deny traffic to port 22, type the following command:
root@d1:~# sudo ufw deny 22/tcp
Skipping adding existing rule
Skipping adding existing rule (v6)Note that since I already had this rule in place, the actual execution was skipped. It the rule did not exist then you would receive “Rules updated” message.
How to Setup UFW Access Rules for IP Address
You can set up rules to allow or deny traffic for specific IP addresses.
How to Allow UFW Access for an IP Address
To allow traffic from a specific IP address, use the following ufw command options.
sudo ufw allow from [IP Address]Replace [IP Address] with the IP address that you want to allow traffic from.
To allow traffic from IP address 192.168.1.1, enter the command:
root@d1:~# sudo ufw allow from 192.168.1.1
Rules updatedHow to Deny UFW Access for an IP Address
To block a specific IP address, use the ufw command options.
sudo ufw deny from [IP Address]Replace [IP Address] with the IP address that you want to block.
root@d1:~# sudo ufw deny from 192.168.1.1
Rules updatedAdvanced UFW Firewall Configuration
In addition to the basic UFW commands, you can also configure UFW for more advanced firewall settings.
Allow Outgoing Traffic on a Port
By default, UFW allows all outgoing traffic. However, there may be times when you need to restrict outgoing traffic. To restrict outgoing traffic, you can use the ufw command with the allow out option, followed by the port number and the protocol.
sudo ufw allow out [port]/[protocol]Replace [port] with the port number and [protocol] with the protocol used by the service. For example, to allow outgoing traffic to port 80, type the following command:
root@d1:~# sudo ufw allow out 80/tcp
Rules updated
Rules updated (v6)Block Outgoing Traffic on a Port
To deny outgoing traffic to a specific port, enter the following ufw command options.
sudo ufw deny out [port]/[protocol]Replace [port] with the port number and [protocol] with the protocol used by the service. For example, to deny outgoing traffic to port 80, type the following command:
root@d1:~# sudo ufw deny out 80/tcp
Rules updated
Rules updated (v6)Block Incoming Traffic from Specific IP Addresses
To block outgoing traffic to a specific IP address, enter the following ufw command options.
sudo ufw deny to [IP Address]Replace [IP Address] with the IP address that you want to block outgoing traffic to.
To block traffic to IP address 192.168.1.1, type the following command:
root@d1:~# sudo ufw deny to 192.168.1.1
Rules updatedLimiting Connections on Specific Ports
You can also limit the number of connections to specific ports to prevent Denial of Service (DOS) attacks.
Limiting Connections to a Specific Port
To limit the number of connections to a specific port, type the following command in the terminal window:
sudo ufw limit [port]/[protocol]Replace [port] with the port number and [protocol] with the protocol used by the service.
To limit connections to port 22, type the following command:
root@d1:~# sudo ufw limit ssh
Rules updated
Rules updated (v6)Customize UFW Settings
You can customize UFW default policies that will change the default behavior of the commands. Use the following ufw command line options to change policy.
sudo ufw default [allow/deny]Replace [allow/deny] with the policy that you want to set as the default.
To set the default policy to deny, type the following command:
root@d1:~# sudo ufw default deny
Default incoming policy changed to 'deny'
(be sure to update your rules accordingly)To change the default behavior to allow all by default use ufw with the following options.
root@d1:~# sudo ufw default allow
Default incoming policy changed to 'allow'
(be sure to update your rules accordingly)Adding UFW Application Profiles
UFW comes with pre-defined application profiles that allow easy configuration of the firewall for specific services. Application profiles are used in case a service application is using more than one port.
To list all ufw app profiles use the command:
root@d1:~# ufw app list
Available applications:
Apache
Apache Full
Apache Secure
CUPS
Nginx Full
Nginx HTTP
Nginx HTTPSHow to Create a New UFW App Profile
To add an application profile, use the following ufw command line options. You need to do create a profile file for your application.
Let’s say I have an app name, MyTestWebServer. I will need to follow 2 steps to create a new application profile.
- Create a new profile file in the folder
/etc/ufw/applications.d/. - Now tell UFW to reload the application definition.
- Restart the ufw firewall.
In my case, I have created a new file named mytestwebserver.profile in the /etc/ufw/applications.d/ folder with the following text:
[MyTestWebServer HTTP]
title=My Test Service (MyTestWebServer, HTTP)
description=Small, test server
ports=80/tcp|8080/tcp|9090/tcpIn this config file, I have defined ports 80,8080 and 9090 for my test web server.
Now reload application definitions.
root@d1:# ufw app update MyTestWebServerIf you re-run the “app list” option you will find that your app profile is available to UFW.
root@d1:/etc/ufw/applications.d# ufw app list
Available applications:
Apache
Apache Full
Apache Secure
CUPS
MyTestWebServer HTTP
# ...rest of the output removed.We can also check the profile details with the following command:
root@d1: # ufw app info MyTestWebServer
Profile: MyTestWebServer
Title: My Test Web Server (MyTestWebServer)
Description: Small, test server
Ports:
80/tcp
8080/tcp
9090/tcpNow with the profile available to UFW, you can activate it with the ufw command options below.
sudo ufw app [name]Replace [name] with the name of the application profile that you want to add.
root@d1:# ufw allow MyTestWebServer
Rules updated
Rules updated (v6)Conclusion
In this post, I went over the basics of the UFW firewall. The examples presented here should cover 90% of the use cases. If you need more detail check out the UFW man page for additional options.