- What is Port Scanning and How Does it Work?
- Purpose of Port Scanning
- Different Types of Port Scans with Examples
- Planning for a Port Scan
- Analyzing Responses From Scanned Ports
- What is a The Three-Way Handshake in TCP
- Methods of Detecting Port Scans
- Ethical & Legal Considerations of Port Scanning
- Download and Share Infographics for Port Scanning
- Conclusion
- Frequently Asked Questions
What is Port Scanning and How Does it Work?
Port scanning is a method that involves the examination of a network’s open and closed ports to identify vulnerabilities and access. Port scanning works by actively or passively accessing a port to find out if it is active or closed.
Port scanning has therefore become a critical tool for ensuring the safety of networks by the admins and a tool which hackers use to find gaps in coverage.
In this post, I will discuss details of port scanning, available tools, and how to reduce instances of network intrusions.
Before proceeding you might want to review what a port is and why they are used.
You can also download and share various infographics related to this post available towards the end of this post.
Purpose of Port Scanning
The purpose of port scanning is to identify which ports on a computer or network are open and which are closed. This information can then be used to determine the weak points of a network and identify associated vulnerabilities.
Port scanning can be used for various purposes, such as:
Network Mapping
Port scanning can help map out the topology of a network and identify the number of hosts and open ports, which can be useful for network administrators to understand the network’s infrastructure
Vulnerability Assessment
By identifying open ports and the services running on those ports, port scanning can be used to assess the security of a network and identify potential vulnerabilities that can be exploited by attackers.
Penetration Testing
Port scanning is often used as a first step in penetration testing to gain initial information about a target system, to determine the targets’ attack surface, and to find potential entry points into the system.
Service and System Testing
Port scanning can also be used by developers and system administrators to test their applications and systems, to ensure they are configured correctly and are functioning as intended.
Detection of Intruders
Port scanning can also be used to detect unauthorized access attempts by attackers attempting to gain entry into a network. By detecting these attempts, network administrators can take appropriate action to secure the network and prevent unauthorized access.
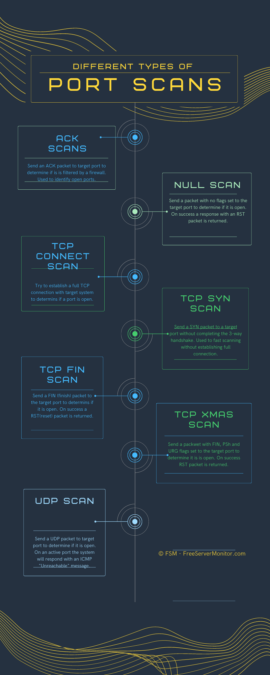
Different Types of Port Scans with Examples
There are several types of port scans that security professionals use to identify open ports and assess network security. Listed below are some of the most common.
For each of these scan types, I will also show actual examples using the nmap utility. Do note that nmap is not installed by default on Linux systems so you will have to manually install it. Use the following command to install the correct nmap package on Ubuntu.
user@mars:~$ sudo apt install nmapACK Scan
ACK (acknowledgment) scan involves sending an ACK packet to the target host to determine if a port is filtered by a firewall. If the port is filtered, the system will not respond. If the port is not filtered, the system will respond with an RST packet, indicating that the port is open.
Example: nmap -p23,80 -sA target-host
user@mars:~$ sudo nmap -p23,80 -sA scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 14:05 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.021s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
23/tcp unfiltered telnet
80/tcp unfiltered httpNULL Scan
NULL scan involves sending a packet with no flags set to the target port to determine if it is open. If the port is open, the system will respond with an RST packet, indicating that the port is closed. If the port is closed, the system will not send a response packet.
Example: nmap -sN target-host
user@mars:~$ sudo nmap -p23,80 -sN scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 14:06 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.021s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
23/tcp open|filtered telnet
80/tcp open|filtered httpTCP Connect Scan
TCP connect scan is the most basic form of port scanning and involves the establishment of a full TCP connection with a 3-way handshake to the target port. If a connection is established, the port is considered open, and if the connection is refused, the port is considered closed.
Example: nmap -sT target-host
sohail@mars:~$ nmap -A -sT scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 13:37 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.033s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 ac:00:a0:1a:82:ff:cc:55:99:dc:67:2b:34:97:6b:75 (DSA)
| 2048 20:3d:2d:44:62:2a:b0:5a:9d:b5:b3:05:14:c2:a6:b2 (RSA)
| 256 96:02:bb:5e:57:54:1c:4e:45:2f:56:4c:4a:24:b2:57 (ECDSA)
|_ 256 33:fa:91:0f:e0:e1:7b:1f:6d:05:a2:b0:f1:54:41:56 (ED25519)
25/tcp filtered smtp
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Go ahead and ScanMe!
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
9929/tcp open nping-echo Nping echo
31337/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.05 secondsOptions for the nmap command:
-A: Enable OS and version detection.- -sT: Do a TCP connect scan.
TCP SYN Scan
TCP SYN or half-open scan involves sending a SYN (synchronize) packet to a target port without completing the full three-way handshake. This type of scan can be used to identify open ports without establishing a full connection and is usually less noticeable to intrusion detection systems and faster to execute.
Example: nmap -sS target-host
user@mars:~$ sudo nmap -p23,80 -sS scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 14:07 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.022s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
23/tcp closed telnet
80/tcp open httpTCP FIN Scan
TCP FIN (finish) scan involves sending a FIND packet to the target port to determine if it is open. If the port is open, the system will respond with a RST (reset) packet, indicating that the port is closed. If the port is closed, the system will ignore the FIN packet.
Example: nmap -sF target-host
user@mars:~$ sudo nmap -p23,80 -sF scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 14:08 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.018s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
23/tcp open|filtered telnet
80/tcp open|filtered httpTCP Xmas Scan
The TCP Xmas scan involves sending a packet with multiple flags, FIN (finish), PSH (push), and URG (urgent), to the target port to determine if it is open. If the port is open, the system will respond with a RST packet, indicating that the port is closed. If the port is closed, the system will not send back any response.
Example: nmap -sX target-host
sohail@mars:~$ sudo nmap -p22 -sX scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 14:02 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.029s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
22/tcp open|filtered ssh
Nmap done: 1 IP address (1 host up) scanned in 0.69 secondsUDP Scan
UDP scan involves sending a UDP connection request to the target port to determine if it is open. If the port is open, the system will respond with an ICMP (Internet Control Message Protocol) Destination Unreachable response, indicating that the port is closed. If the port is closed.
Example: nmap -p80 -sU scanme.nmap.org
sohail@mars:~$ sudo nmap -p80 -sU scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 14:01 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.022s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE
80/udp closed http
Nmap done: 1 IP address (1 host up) scanned in 0.35 secondsOptions for the nmap command:
-p80: Run a scan on a specific port. If you want to use multiple ports then separate them by using a comma(,).- -sU: Do a UDP scan.
Version Scan
Version scan allows determining the version of software running on the target system.
Example: nmap -A scanme.nmap.org.
sohail@mars:~$ nmap -A -p80 scanme.nmap.org
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-11 13:57 PST
Nmap scan report for scanme.nmap.org (45.33.32.156)
Host is up (0.022s latency).
Other addresses for scanme.nmap.org (not scanned): 2600:3c01::f03c:91ff:fe18:bb2f
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Go ahead and ScanMe!
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.00 secondsnmap options used:
-A: get operating system or service information for a specific host/port.-p80: Run a scan on a specific port. If you want to use multiple ports then separate them by using a comma(,).
For all options on using nmap, check the documentation.
Planning for a Port Scan
Port scanning works by sending packets set with flags to specific ports on a target system and analyzing the response to determine if the port is open or closed. Not all requests for a port scan result in a response. That may mean that either the port is not open or the client IP address accessing the host is blocked.
The process of port scanning involves the following steps:
- Select Target Systems: Identify one more hosts you are targeting
- Select Port(s): Select specific ports for scanning.
- Identify a Scan Type: The next step is to generate packets specific to the test type planned for execution.
- Send Scanning Traffic: Using one of the port scanning tools like
nmap, send the scan requests to the target system. - Collect Response Data: Collect responses from the target system, in cases, where there is no response that is also a valid test usually identifying a closed port.
- Result Analysis: Analyze the response result to complete vulnerability analysis.
Analyzing Responses From Scanned Ports
To analyze responses from the port scanning results one needs to look at the following metrics.
- Port Status: Check the state of the port. The common status are open, closed and filtered. Open ports are those where services are actively listening for incoming connections. Filtered ports are those which are blocked by a firewall.
- Service Information: This shows standard service name if available. For example, if port 80 is active then the service shown will be HTTP.
- Operating System Information: Here you can get info on the operating system and version number. This can be helpful to know as certain versions of operating system maybe have open bugs that makes them vulnerable.
- Firewall Information: Provides information about the type of firewall, including the rules in place. This information is useful in determining the types of target attacks.
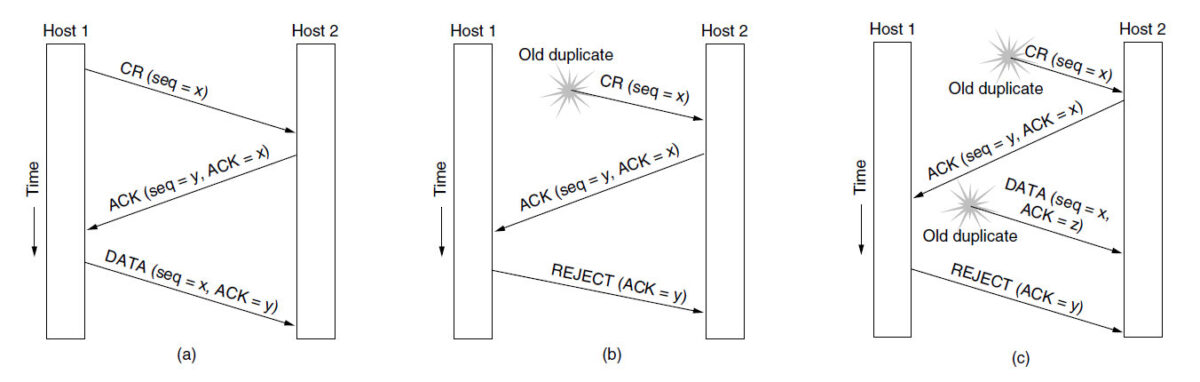
What is a The Three-Way Handshake in TCP
A 3-way handshake is a process used during the initial connection on a TCP socket. Following steps are executed in order:
- SYN (Synchronize): SYN request is sent to the target host to initiate the connection. The SYN packet contains a unique identifier or sequence number.
- SYN-ACK (Synchronize-Acknowledgment): If the target port is accepting connections, a SYN-ACK response will be returned. This request contains the sequence number and confirms the establishment of a connection.
- ACK (Acknowledgment): ACK request is sent back to complete the three-way handshake. The ACK response contains the target system’s sequence number and confirms the SYN-ACK response.
Methods of Detecting Port Scans
Port scans from third parties are a significant security threat, as they can be used to gather information about a target system vulnerabilities for malicious purposes.
Liste below are some methods of detecting a port scan. Some of these are active or real-time, while others are passive.
Behavioral Analysis
Behavioral analysis relies on the behavior of the client’s requests. For example, if there is a sudden increase in traffic from a particular IP address then that IP is flagged or may be temporarily blocked from accessing local resources.
Another example would be frequent failed login attempts from an IP address.
Firewalls
Firewalls are used to block or filter incoming network traffic. Rules are configured to set up the filtering of traffic on ports.
An example would be a firewall on a port that only allows HTTPS traffic and blocks all other types of traffic. When such a rule is set up, then a request for login to a database on port 3306 will be blocked from all IP addresses.
Honeypot Decoy
A honeypot is a decoy system that is set up to lure attackers away from the actual target port.
By detecting and tracking the activity of attackers targeted at the honeypots one can gather information on the location and methods of the attackers.
Hybrid Detection Systems
Hybrid detection use one or more methods available to create a system of detecting networked intrusion. Usually there is a combination of network analysis, IP reputation and log analysis done simultaneously to identify if a system vulnerability is being exploited.
Using the multiple detection method approach provides a more effective response to detecting port scan and network intrusion.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) are software tools designed to detect and alert on potential security threats. Most IDS systems use the hybrid approach to detection of active and passive port scanning.
On identification of suspicious behavior, notifications are sent to administrators. Access to systems could also be disabled temporarily until the issue of potential intrusion is resolved.
IP Address Reputation
IP address reputation is a method of detecting security threats based on the reputation of the source IP address.
Blaclist databases are set up by multiple companies that maintain records of Ip addresses and domain names associated with malicious activity.
You can check our blacklist tool to check IP reputation.
Log Analysis Systems
System log analysis tools are used to analyze and detect network intrusion and port scanning actions. These systems are considered passive as most of the log analysis is not done in real-time.
By analyzing the logs, patterns of suspicious activity can be discovered.
Network Traffic Analysis
Network traffic analysis allows for the ability to monitor in real-time data flowing through a network. For example, if someone is actively using the aforementioned port scanning techniques, it can be easily identifiable if there is suddenly an ACK Scan or TCP Connect Scan attack in place.
Source Port Randomization
With Source port randomization, the outgoing traffic port is randomly changed to make it difficult for an attacker to distinguish between open and closed ports.
By using source port randomization, network administrators make it more difficult for attackers to conduct port scans thus increasing the security of their network.
Check the details of each of these methods in scanning methods post.
Ethical & Legal Considerations of Port Scanning
Port scanning is a widely used tool for security testing and vulnerability assessments, but it is also a controversial issue in the world of cybersecurity due to its potential for abuse. There are ethical and legal considerations that must be taken into account when conducting port scanning activities.
Ethically, it should be understood that one should only freely conduct port scanning on systems they own or have permission to. It is not ethical to scan systems without prior permission from the owner. Doing so could result in legal consequences for the network executor of such a scan.
Read our upcoming post on the ethical and legal impacts of hacking for more details.
Download and Share Infographics for Port Scanning
Conclusion
Having open networks raises the probability of a serious attack on an organization which at the least has financial implications and at words can land an organization in legal trouble.
Analyzing your network access for both internal and external functions is critical in securing your organization’s data and reducing the chances of becoming a victim of cybercrime.
Frequently Asked Questions
What is the Different between TCP and UDP?
In TCP/IP, a TCP port is connection-oriented where as the UDP port is not considered connection less. This is because TCP uses a sliding window protocol to ensure the delivery of network packets that may be lost during data transfer.
UDP does not provide any such guarantee and there the application itself will need to build a mechanism to request lost packets.
Check out our post on port numbers to get more details.
What are some common port numbers?
Some of the common port numbers are 80 for HTTP and 443 for HTTPS. There are other ones such as port 3306 for the MySQL database.
For a more comprehensive list or port numbers and services using them check here.